Event monitoring gives you the ability to see how users are interacting with Salesforce in a whole new way. In today’s world, a large number of security threats can come from inside your organization. Your users may have access to lots of sensitive customer information that is susceptible to theft or unauthorized access. With the introduction of real-time events, you will be able to take instant action and add a whole new level of security to your Salesforce Org.
What is event monitoring?
Event monitoring is a capability within Salesforce to collect, analyze, and manage the usage of the application. Each time an action is initiated, like a page view or report run, an event is recorded and added to the event log. This gives you a thorough look into how users interact with Salesforce as there are 49 different event types collected. These events can range from Apex executions to page views. You can access the events in the form of an event log file through the Lightning Platform REST and SOAP APIs. Though as we are talking about incredibly large volumes of data, it is only made available on a daily basis or hourly basis and stored for 30 days.
Introducing real-time events
A recent addition to event monitoring is a subset of events that are available in real-time, aptly named real-time events. This new functionality takes some of the events that would normally be logged and streams them using platform events. This means that you can consume the events in the same way that you do for platform events, via an external subscriber. Different from platform events, not all real-time events can be subscribed to via triggers or declarative tools.
A practical example: monitoring page access
A common use case of real-time events is an organization that is required to track access to sensitive health data that is stored in Salesforce. Each time a user accesses a page, a Lighting URI Event is created and streamed to its subscribers. The event contains the page identifiers, user information and session details of the page view.
Example Event: LightningUriEvent
As you can see in this example event, we can begin to piece together details around how this user was interacting with Salesforce. You can see that they have viewed a patient’s history – this is indicated by the queried entity and the operation values. The user navigated to the patient history page from a contact record while they were using their patient consultations app. We can see the details of the user that initiated the transaction as well as a number of details around their connection and device.
Real-time event types
There are five primary event types that are included with event monitoring.
Authentication – The Login & Logout events allow you to identify numerous characteristics of a user’s session. This type of data can be used to spot anomalies in the user’s browser version or a high volume of login attempts. You can also track the sessions in which an admin has logged in as another user.
Data Access – When a user accesses data as a report or list view, each action that takes place is fired as an event. For example, when a user adds a field to a report or runs an export. All API transactions are also sent.
Page Access – As mentioned in our earlier example, every time a user accesses a page, an event is fired.
Threat Detection – New in the Summer ’20 release, these are a series of events that take aggregated event log data, and are fired when a security vulnerability is detected. The attacks being analyzed for are credential stuffing, report anomalies, and session hijacking.
Mobile Security Events – As part of Enhanced Mobile Security (licensing required), there are an additional subset of events related to mobile app use that are included as real-time events. For example, the MobileScreenshotEvent is published each time a user takes a screenshot of their mobile device while using the Salesforce mobile app.
Enabling real-time events
To get started with real-time events, head to setup and into the quick find search for ‘Event Manager’. Enterprise and Unlimited environments have access to the Logout Event by default, but the remainder of the events need licensing to access Shield Event Monitoring. If you don’t have access and would like to try them out, you can enable real-time events in a developer edition org. In order to activate the events, simply navigate to the event that you would like to use and enable streaming or storage. Once enabled, there are three key ways that you can take advantage of the events: streaming them, storing them in big objects, and using them to evaluate transaction security policies.
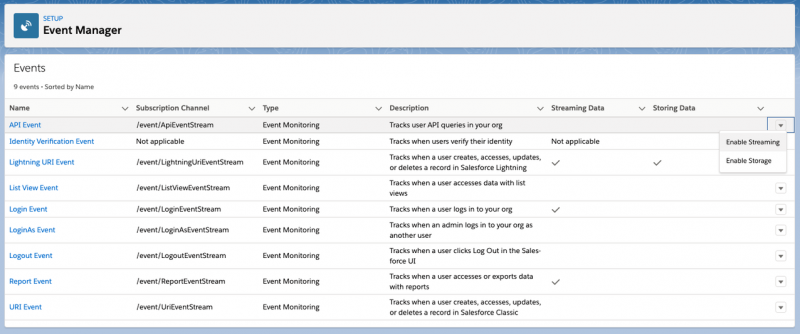
Streaming real-time events
As mentioned before, real-time events are streamed using platform events and can be consumed by any relevant client application. For example, if you are using a third party application for monitoring, you can subscribe to the real-time events and evaluate them there. A great way to explore the events is to use Streaming Monitor App provided by Salesforce Labs! Streaming Monitor allows you to select the type of event and then subscribe to a number of events using the lighting-emp-api component. If you would like to learn more about this, check out this blog post by Philippe Ozil on Salesforce’s streaming capabilities.
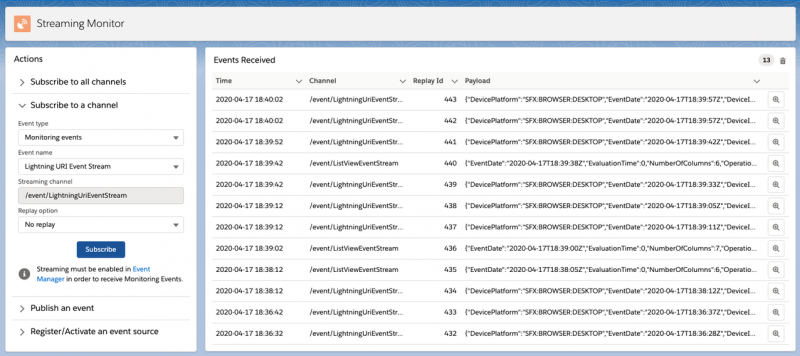
Storing real-time events in big objects
In addition to subscribing to the events, you can store them directly in your Salesforce org. They are pushed into a big object table that has been preconfigured for each event type. Once enabled, the events will be stored and available for six months from the point the event occurred. The big object records can be accessed via Async SOQL, through the RESTful interface or via SOQL if you have the primary index and event date. Continuing on from our earlier example, a healthcare organization can use big objects to store every page view that occurs into the Lighting URI Event big object table.
Enhanced transaction security
Enhanced transaction security gives you the ability to monitor a selection of real-time events and evaluate them against a specified policy. If the policy’s criteria are met, you have the ability to block the user from completing the action and/or sending an email to a designated user. Currently, you can write transaction security policies for the API event, list view event, login event, and report event. A basic use case would be to block any user from downloading a report containing personal contact information. An example of an Apex policy would be calling out to an external database to validate a community user’s login characteristics.
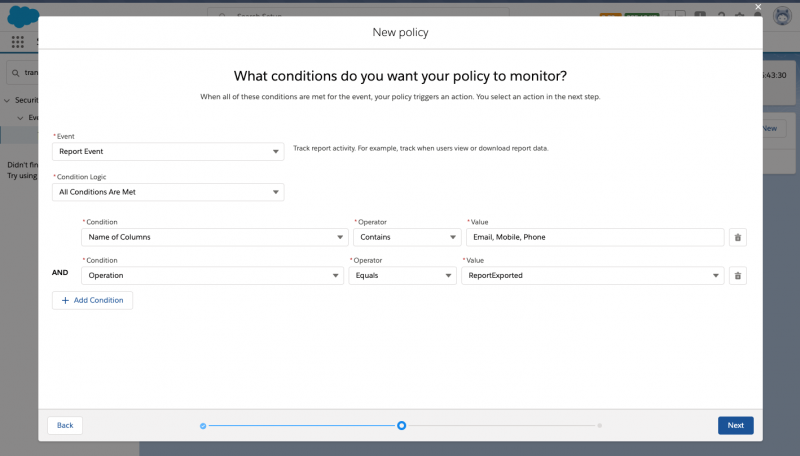
Conclusion
As you can see – event monitoring provides an excellent layer of security and a plethora of potential data at your disposal. Stay tuned for our next Event Monitoring blog post where we’ll be taking a deep dive into Enhanced Transaction Security Policies!
If you would like to learn more about event monitoring and real-time events, check out the listed resources and trailhead modules.
Trailhead
Event Monitoring
Platform Event Basics
Documentation
Full List of Event Monitoring Events
Getting Started with Real-Time Events
Full List of Real-Time Events
About the author
Stephan Chandler-Garcia is a Senior Developer Evangelist at Salesforce. He focuses on Application development, Security and Communities. You can follow him on Twitter @stephanwcg