In our Introducing Salesforce Private Connect blog post, we learned about our customer’s challenges and the benefits of Private Connect. In short, businesses need data from multiple clouds to operate. However, connecting data over those clouds in a secure and compliant way can be time consuming, manual, and error-prone. Salesforce Private Connect is a fast, easy, and secure way to connect Salesforce orgs with AWS data centers. Salesforce developers can set up the connection quickly and easily in a point-and-click interface. In this post we’ll guide you through how to set up Private Connect and configure inbound/outbound private connections.
Private Connect allows you to do the following:
- Keep communications private
Private bi-directional connections between Salesforce and AWS without exposure to the public internet - Leverage Salesforce enterprise security
Bring disparate systems and data sources together in a seamless workflow - Improve productivity
Simplified setup, configuration and maintenance for developers or admins
Salesforce Private Connect is generally available in the Summer ’20 release in the Americas.
How to set up Private Connect
Now let’s walk through how a Salesforce developer would set up a private connection.
Acme Products, Inc, is a fictional West-coast based supplier of automobile components and systems. To manage their parts inventory, financials, and shipping, Acme Products uses an ERP implementation in AWS that includes the Amazon Elastic Compute Cloud (Amazon EC2) for the compute layer running in a Virtual Private Cloud (VPC). Acme Products is also heavily invested in Salesforce. To manage their sales motions and call center activities, they use Salesforce Sales Cloud and Salesforce Service Cloud respectively.
Acme Products sends a significant amount of traffic between Salesforce and AWS in both directions to keep these critical systems aligned. To avoid sending this traffic through the public internet and making it vulnerable to attack, Acme Products decides to leverage Salesforce Private Connect to keep their traffic safe and secure.
Whenever there is a product change in their ERP system (price change, description change, new product offering and so on), Acme Products sends these changes to Salesforce to keep their products and price books up to date in Sales Cloud, as well as ensure that their sales team is offering accurate quotes to their customers. Acme Products needs to create an inbound private connection to Salesforce in order to send this traffic privately.
Inbound private connections
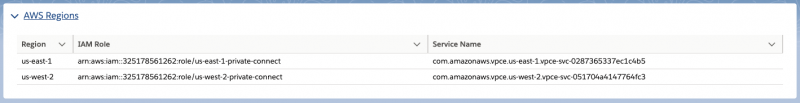
The first step is to create a AWS PrivateLink endpoint inside of their ERP VPC in AWS that sends traffic to the Salesforce managed VPC. Melissa, the Salesforce admin at Acme Products, looks up the Salesforce endpoint service name running in their region inside of the Salesforce setup UI of Private Connect.
Melissa provides this service name to Arjun, the AWS administrator at Acme Products. Arjun uses the service name to create a PrivateLink endpoint inside the ERP VPC. He also selects the ERP VPC, the availability zones the endpoint will run in, and the security groups allowed to access the endpoint as part of the PrivateLink endpoint setup.
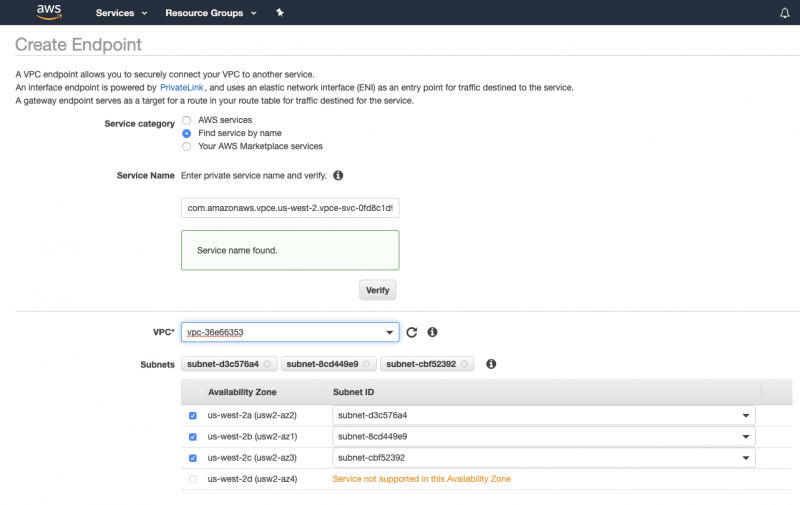
Once the endpoint is created, Melissa needs to accept it inside of Salesforce. Arjun passes the VPC endpoint ID back to Melissa, who then uses it to create an inbound private connection inside Salesforce. She creates an inbound connection (in this case) as the traffic initiates inside of AWS and flows into Salesforce.

The final step before Acme Products can send traffic through this private connection is to map the Salesforce My Domain name to the VPC endpoint IP address in AWS using Route53 as a hosted zone. This redirects any traffic coming from the ERP VPC endpoint to this particular Salesforce Org (as My Domain names are unique) through the private connection. Once the DNS mapping is in place, the ERP can make calls into Salesforce using the standard Salesforce APIs and be redirected through the private connection. No code changes needed!
Outbound private connections
As mentioned previously, the Salesforce Private Connect feature is bidirectional. Let’s assume a customer of Acme Products has inquired through a case as to the status of their order and if they can still make an adjustment. The call center representative can make a real-time API call into the ERP through the private connection only once an outbound private connection is established.
To setup an outbound private connection, Melissa, our Salesforce administrator, provides the Identity and Access Management (IAM) role for the region where the AWS endpoint service is running to Arjun. The IAM role is available in the regions dropdown inside of the Salesforce Setup UI (see first image above). Arjun adds this IAM role to the allowlisted principles tab of the endpoint service. By doing this, Arjun is granting access to the Salesforce Managed VPC service inside of AWS.
Once the above step is complete, Arjun provides Melissa with the AWS endpoint service name that is exposing the private ERP API. Melissa can now create the outbound connection in the Salesforce Setup UI.

Melissa’s outbound connection creates an AWS PrivateLink endpoint that Arjun will need to accept within the AWS Console. Once accepted, the outbound connection will move through the provisioning process until finally reaching a “Ready” status, which means the connection is available to accept traffic.
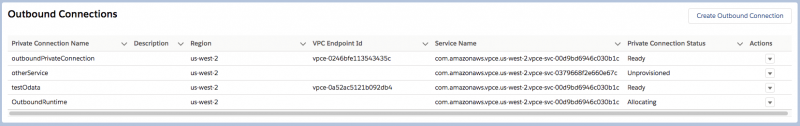
To determine which outbound traffic should flow through the private connection, Melissa must set up a Named Credential inside of Salesforce. Named Credentials are a powerful integration framework that allow administration and runtime handling of authentication credentials for web service calls. The main benefit is that Named Credentials allow authentication credentials to be decoupled from your code, making them easier to maintain. In Summer ‘20, there is a new lookup field on the Named Credential that allows Melissa to specify the outbound network connection she wants to utilize. Now, any callouts from Salesforce using this Named Credential will be routed through the private connection instead of over the public internet.

Now that the Named Credential is set up, Melissa can use it in any of her outbound workflows. For instance, she can reference this Named Credential from an Apex callout using the Apex syntax “callout:<nameOfNamedCredential>” which in her case would be “callout:PrivateAwsService,” so that any Apex callout traffic flows through the outbound private connection. She can also use this Named Credential in External Services, Salesforce Connect, or any other place a Named Credential is supported for outbound authentication.
Salesforce Private Connect is generally available in the Summer ’20 release in the Americas. To get started now, reach out to your Salesforce Account Executive or visit https://www.salesforce.com/aws for more information. Interested in the architecture? Learn more by watching the AWS Private Connections recorded Dreamforce 2019 session. There, you can also see a demo of the product. Want a step-by-step detailed guide on how to set up Private Connect? Read the Private Connect Product Documentation. Lastly, Private Connect is available in Amazon AppFlow as a connection option for Salesforce allowing for quick, private integrations with select Amazon services.
We are also collecting product feedback to determine what Private Connect features to support next. To voice your input on important topics such as AWS region support or Salesforce Cloud support, please fill out this Private Connect Product Roadmap Survey here.
About the author
Courtney Dascenzo is a Product Manager at Salesforce covering Platform Integrations and Platform Data Services.
