Agentforce operates in advanced messaging channels to assist customers by addressing their questions. Agentforce agents can autonomously act on behalf of customers, performing valuable actions, such as creating a case or booking a flight. However, proper implementation is crucial to avoiding potential security risks. To protect against malicious users attempting to access or manipulate sensitive data, user authentication and authorization are essential for agents to complete certain actions on behalf of the user.
In this blog post, we’ll explore how to securely implement private agent actions using authentication via the MuleSoft API, ensuring that your Agentforce agents operate safely and effectively.
What are Agentforce actions?
Agentforce agents can take two types of actions: public actions and private actions.
Public actions
Public actions can be taken on behalf of anyone, regardless of identity, so they require no authentication. For example, the Answer Questions with Knowledge action can be a public action if it’s grounded in public information, such as a company’s return policies.
Private actions
Private actions can only be taken on behalf of specific users, so they do require authentication. Developers would determine which actions are private based on their company’s security standards. Common examples include updating personal appointment information, making purchases, or requesting services on a support contract. To complete a private action, Agentforce must ensure that the user is authorized and that their identity is securely confirmed.
Using a One-Time Password (OTP) authentication approach via MuleSoft, we can establish a user’s identity with an Agentforce agent and authorize the agent to implement private actions.
How to enable OTP-based user authentication
An effective approach to authenticate users with Agentforce is by leveraging MuleSoft for an OTP-based authentication mechanism. This solution allows Agentforce to securely verify users by sending a one-time password (OTP) via email, phone, or other channels. The user must then provide this OTP to the agent for identity confirmation.
A typical OTP authentication flow includes the following steps:
- Pre-chat interaction (optional): The agent collects basic user information, such as name, email, etc.
- Reconfirmation: The agent reconfirms the information with the user to ensure its accuracy.
- OTP generation: Upon user confirmation, the agent generates a one-time password via the MuleSoft API and sends it to the user via email.
- User authentication: The user enters the OTP into the chat, which is then compared on the backend with the one generated by the agent.
- Validation: If the OTP match, the user is authenticated.
- Data encryption: All sensitive data, such as the OTP and user information, can be encrypted or masked and stored for auditing and monitoring purposes.
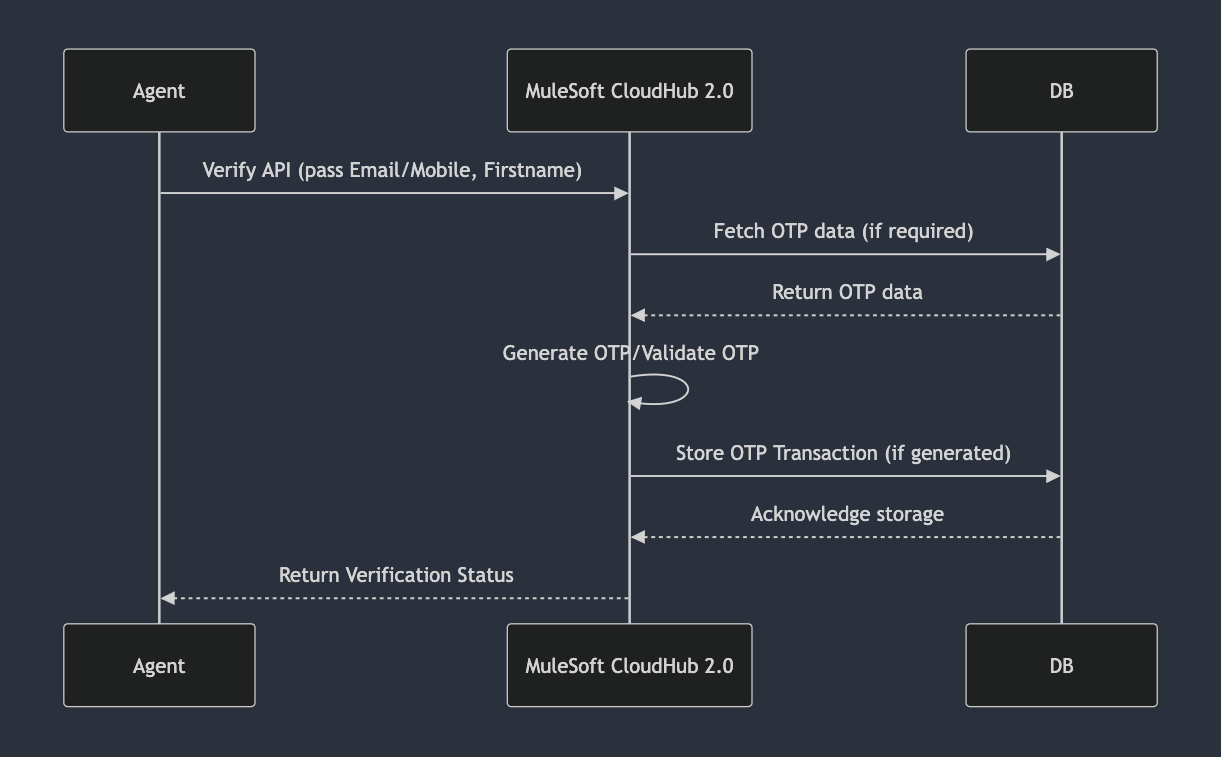
Steps to implement authentication
When implementing authentication, you’ll be modifying your agent’s interface to include a visible pre-chat form or a dedicated topic for collecting user information and initiating the OTP process. This will involve the following steps.
- Requesting user information: When a conversation starts, the first step is to collect the first name, last name, and email or mobile number from the user. As shown in the screenshot below, you’ll use a custom topic to collect user details (first name and email) and call an action (flow) that triggers a MuleSoft API to generate and validate the OTP.
Note: You can provide instructions to accept only valid domain email IDs and include logic to re-validate the domain in your implementation.

- Reconfirming user details: To avoid errors, the agent reconfirms the information provided by the user before sending them an OTP.
- Generating and sending the OTP: The user confirms that their first name and email ID are correct, so that the agent can proceed to generate the OTP and send it to the user via email.
Note: The Messaging Session object ID will be sent as part of the request to the MuleSoft API to identify the OTP for a specific user, as the Messaging Session object ID is unique.

The user will receive an email with an OTP that is valid for 90 seconds. This duration can be configured in the MuleSoft implementation using the OTP creation timestamp and the OTP validation request timestamp.

The MuleSoft API will send the status response, along with the messaging session ID, first name, and email ID that was included in the request.

- Validating the OTP: Once the user enters the OTP into the agent chat interface, an agent action is triggered to validate the OTP using an autolaunch flow. This flow calls the MuleSoft API that retrieves the OTP from the database corresponding to the messaging session ID, as shown in the screenshot below.
Note: The collected user information and OTP will be securely stored against the messaging session ID for audit trails and validation in the database. This ensures that any authentication attempt can be reviewed for security purposes.

- Executing the private actions: A flow retrieves the OTP validation status from the MuleSoft API and confirms the status back to the agent.

Private topics, which are sensitive in nature, can be configured to require user authentication. The system will prevent execution of these topics unless the user has passed the authentication process, ensuring that unauthorized actions are blocked.
Note: For the OTP flow, you can build a custom solution as we’ve discussed here or use a third-party vendor solution like Twilio.
Key benefits of user authentication
The key benefits of user authentication with Agentforce include:
- Enhanced security: By introducing OTP-based user authentication, this solution ensures that only authorized users can perform private actions, mitigating the risk of unauthorized access
- User-friendly process: The OTP process is simple and familiar to users, providing a smooth experience while maintaining a high level of security
- Audit and monitoring: Storing encrypted or semi-masked data for auditing purposes ensures that every authentication attempt can be traced and analyzed, adding an additional layer of accountability
- Scalable and flexible: The solution can be adapted to various use cases and integrated with existing agent workflows without major overhauls
Conclusion
By leveraging the MuleSoft API for OTP-based user authentication in Agentforce, you can ensure a secure and seamless user experience and safeguard sensitive data while enhancing customer interactions in Agentforce.
Resources
- Learn more about Agentforce
- Introducing MuleSoft for Agentforce: API Catalog
- Learn more about Agentforce 2dx
- Learn more about MuleSoft
About the authors
Gopalakrishnan TV is a Lead Member of Technical Staff at Salesforce. He is an API expert, with a decade of experience in MuleSoft. Connect with him on LinkedIn.
Bharath Kumar NJ is a Member of Technical Staff at Salesforce. He is experienced in building enterprise integrations, and he actively contributes to the MuleSoft community as a Trailblazer Guide. Connect with him on LinkedIn.
Nirbhay Sharma is a Member of Technical Staff at Salesforce with experience in enterprise integration & automation. Connect with him on LinkedIn.