Troubleshoot Issues on iOS Apps
This article provides information about troubleshooting issues on iOS apps.
App submission errors can occur when you’re publishing your apps to App Store Connect. These errors include an error message from Xcode or during Apple’s app review.
We identified one or more issues with a recent delivery for your app, “[app name]”. Your delivery was successful, but you may wish to correct the following issues in your next delivery:
Missing Purpose String in Info.plist File - Your app’s code references one or more APIs that access sensitive user data. The app’s Info.plist file should contain a
NSLocationAlwaysUsageDescriptionkey with a user-facing purpose string explaining clearly and completely why your app needs the data. Starting Spring 2019, all apps submitted to the App Store that access user data will be required to include a purpose string. If you’re using external libraries or SDKs, they may reference APIs that require a purpose string. While your app might not use these APIs, a purpose string is still required. You can contact the developer of the library or SDK and request they release a version of their code that doesn’t contain the APIs. Learn more (https://developer.apple.com/documentation/uikit/core_app/protecting_the_user_s_privacy).
This error can occur even if you aren’t using Location Messaging. If you aren’t using the SDK’s location messaging functionality, your users aren’t prompted to provide location permissions. This error occurs because the SDK includes references to CoreLocation.framework. During the app review process, the automated binary scanning detects these references and requires you to provide purpose strings.
If you aren’t using Location Messaging, add a purpose string to your app’s Info.plist file as a placeholder, as shown in this example.
To ensure the proper configuration of your Apple Push Notification Service (APNs) connection and delivery of push notifications for different types of app builds (development or production), keep these points in mind.
-
APNs Server Selection: If you select the Development option, Marketing Cloud Engagement attempts to contact the Sandbox APNs server, regardless of whether you use a
.p8key or a.p12certificate. If you select the Production option, Marketing Cloud Engagement attempts to contact the Production APNs server. -
Apps Built Using Development Certificates: To send notifications only to those devices with apps on
Debugconfiguration, select Development on the MobilePush Administration page in Marketing Cloud Engagement.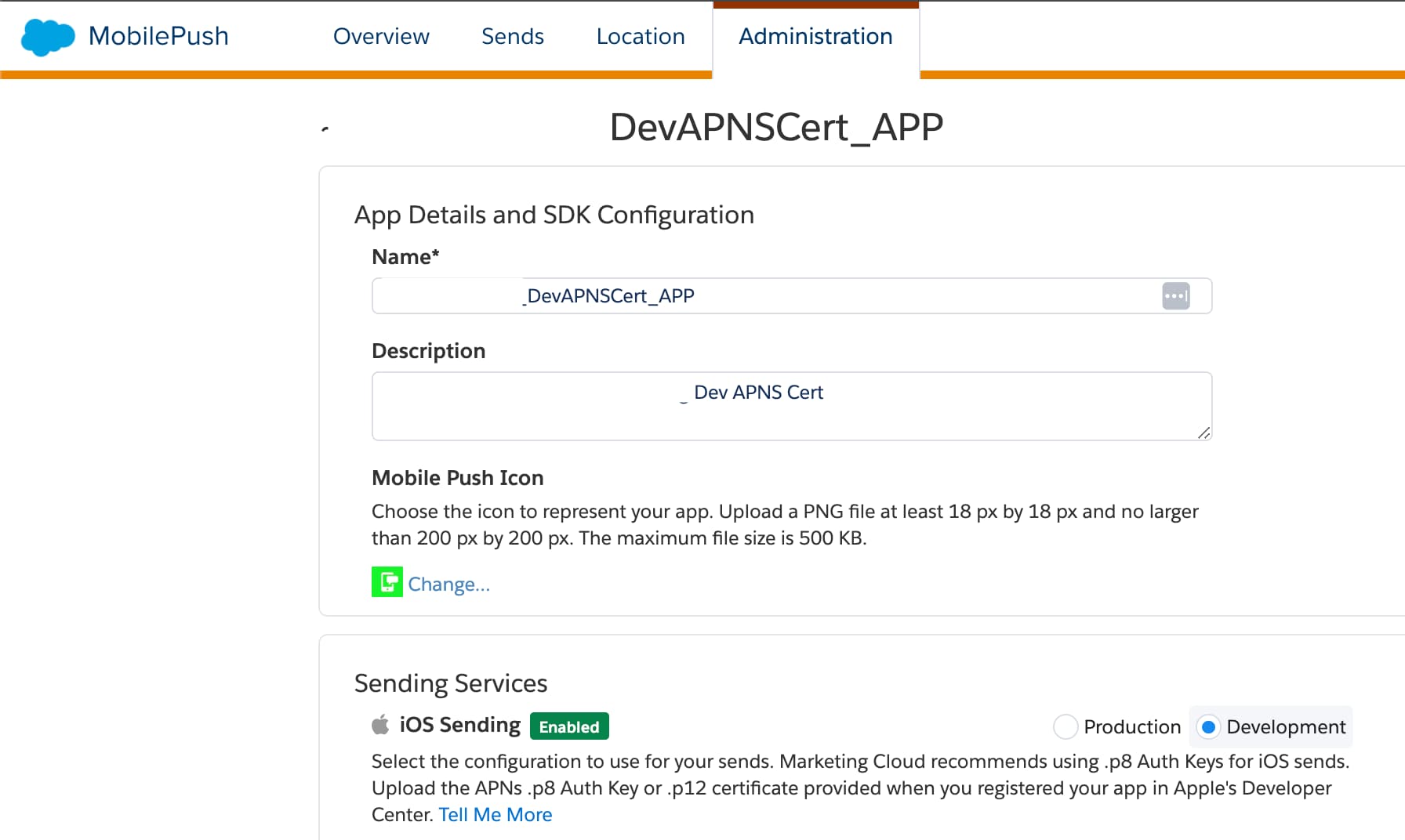
-
Apps Built Using Production or Distribution Certificates: To send notifications only to those devices with apps on
Releaseconfiguration, select Production on the MobilePush Administration page in Marketing Cloud Engagement.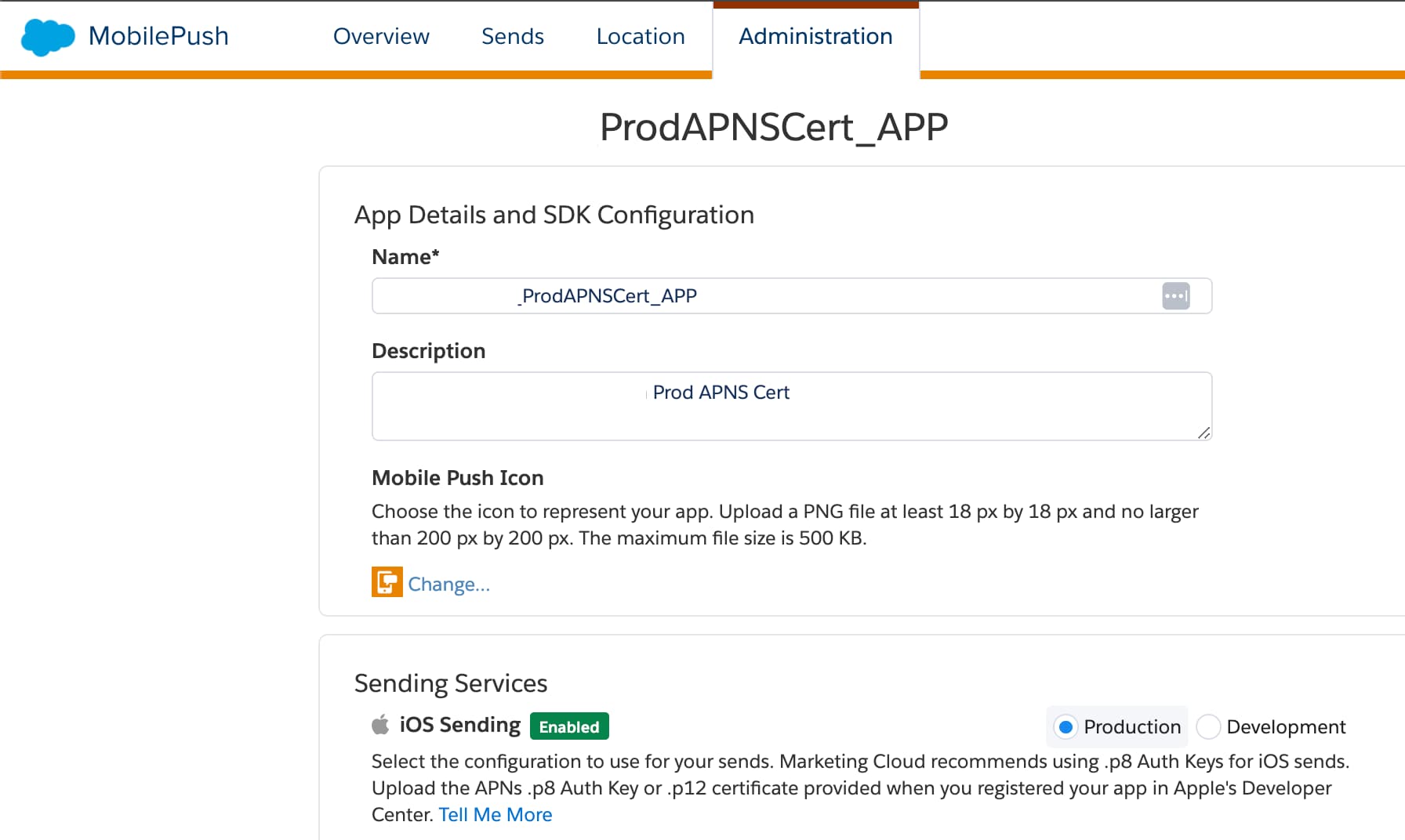
If you encounter issues receiving messages in your app, consider these troubleshooting steps:
- Check the SDK’s log output
- Send a test push
- Evaluate the SDK’s state
- Unblock Network Ports
- Review Additional Troubleshooting Guidance
The MarketingCloudSDK.framework uses extensive internal logging to record actions performed by the SDK for informational and diagnostic purposes.
General, default-level logging is always enabled. Additionally, the SDK writes error and fault-level logs when certain conditions occur. Add this code to your app to enable logging.
If you use SDK versions older than version 8.x, enable logging after SDK configuration.
You can also enable logging with CustomLogOutputter, as shown in this example.
Alternatively, you can enable logging with a standard log output and a log filter, as shown in this example.
To clear previously set filtering options, use this code.
To query the state of debug-level logging, use this code.
The SDK sends all logging output to Apple’s unified logging system. Review this information using Xcode’s Devices and Simulators window or the macOS Console application. If SDK debug logging is enabled, the SDK uses the OS_LOG_TYPE_DEBUG value. Disable logging before you submit a release build to the App Store.
For more information about unified logging, see Logging on Apple Developer.
To test whether your app can receive a push directly from the Apple Push Notification Service (APNs), follow these steps.
-
Get the push token from the SDK. For testing and troubleshooting purposes, retrieve your device token from a running app by calling
sfmc_deviceToken()and send the result to yourself via email, alert, or another method. -
-
Trigger the APNs API directly from the command line if using a
.p8authentication key.This bash script points to the
developmentAPNs service by default. To trigger push from the APNs production server, change the value of theendpointvariable tohttps://api.push.apple.com. -
If you use a legacy
.p12certificate, trigger the APNs API directly from the command line.If your device receives the push notification, the app is configured correctly. The setup includes creating a
.p8authentication key or.p12certificate, building the app with the correct bundle ID, and using the appropriate provisioning profiles.
Note the environment (development or production APNs) in which the push was successfully delivered while sending a test push.
On the Engagement Administration page, point to the same environment under Sending Services > iOS Sending and send a push notification. Check if your device received the push notification.
Ensuring the selection of the correct APNs environment is crucial for the SDK to trigger push notifications to the appropriate APNs server. If you select Development on the MobilePush Administration page, Marketing Cloud Engagement contacts the Sandbox APNs server. If you select Production, it contacts the Production APNs server.
To retrieve a list of all the information the SDK has and its current state, implement getSDKState(), as shown in this example.
The SDK outputs a JSON string as shown in this example.
Testing your app while connected to a corporate network can prevent your test device from receiving messages, especially if your firewall blocks certain ports. Unblock these TCP ports to ensure that your test device can reach the APNs servers.
| TCP Port | Description |
|---|---|
| 5223 | Used by devices to communicate to the APNs servers |
| 2195 | Used to send notifications to the APNs servers |
| 2196 | Used by the APNs feedback service |
| 443 | Used as a fallback service for Wi-Fi devices when those devices can’t communicate with the APNs service on port 5223 |
Refer to these article when you test your app, or to troubleshoot message delivery issues.
- Apple Developer: Technical Note TN2265: Troubleshooting Push Notifications
- Download: APNs Debugging Provisioning File
- Apple Developer: APNs Port Functionality Information
The MobilePush SDK can coexist and work in the same app as the SDKs of other push providers. However, we recommend checking with your other SDK vendors to ensure they also support a multi-push provider implementation. Consider these factors if you implement multiple push SDKs.
Some MPP implementations can prevent the transmission of device tokens and push messages.
Without device tokens, the SDK doesn’t register the device properly. As a result, Marketing Cloud is unable to send push notifications to the device. The SDK expects you to pass push notifications to the setNotificationRequest method. Using this method makes the SDK aware of the notifications and lets it handle them accordingly.
Apple has specific delegate methods that the consuming application must implement to register with APNs and receive push notifications. Implementing multiple push providers can affect the previously mentioned functionality since other vendors can provide wrapper methods for registration and receiving the notifications. Consuming applications often listen to the wrapper methods instead of actual Apple-provided delegate methods. An example of a common issue is when registration with Apple is done for one push provider without setting the deviceToken for other push providers.
Method Swizzling is the process of changing the implementation of a selector at runtime. If Method Swizzling is enabled, other push providers automatically intercept all the application delegate methods, which differ from the normal flow in setting up the deviceToken and notification userinfo.
Method Swizzling can confuse MobilePush SDK users about how and where to set the SDK’s required API methods because another provider is changing the implementation without their knowledge.
To determine if other SDK providers use Swizzling, check to see if they use these methods.
func application(_ application: UIApplication, didReceiveRemoteNotification userInfo: [AnyHashable : Any], fetchCompletionHandler completionHandler: @escaping (UIBackgroundFetchResult) -> Void)func application(_ application: UIApplication, didRegisterForRemoteNotificationsWithDeviceToken deviceToken: Data)
MobilePush SDK users can handle MPP implementations regardless of whether Swizzling is enabled.
If Swizzling is enabled, implement the other push provider’s delegate methods and then implement the MobilePush SDK methods.
First, configure the SDK along with the other Push provider, as shown in this code example.
Next, configure the SDK to set the device token, as shown in this code example.
When Swizzling is enabled in the other push provider, respective delegate methods are intercepted. For example, if Firebase is the other push provider, when a push notification is received from Firebase, the payload received in the UNUserNotificationCenterDelegate’s didReceive notification method is altered to receive a MessagingMessageInfo object. Because the payload doesn’t match the format that the SDK expects, the message isn’t reported.
API:
setNotificationUserInfo(userInfo)setNotificationRequest(response.notification.request)
Notification messages from other providers are displayed in the device’s notification center. However, any action on the notification message from the SDK (for example, URL handling and reporting) doesn’t work.
To disable Swizzling, refer to the other push provider’s documentation. When Swizzling is disabled in the other push provider, the default AppDelegate methods are called.
Implement AppDelegate Methods
MPP implementation issues are often caused by issues related to device registration, badging, geolocation, custom payload keys, and feedback.
-
Registration: You must only make one call to a push SDK to register for push notifications. Otherwise, a single push notification can trigger multiple notification banners, alerts, or sounds. The MobilePush SDK gives the app developer the power to register.
-
Notification Settings: An app can invoke
requestAuthorizationWithOptionsandregisterForRemoteNotificationsmultiple times. However, only the settings from the last call are used, as each successive call overwrites the previous settings. -
Badging: There’s no way to guarantee the value of a badge.
-
Custom Payload Keys: If your implementation must distinguish between two notification providers, use custom keys or other payload-specific data to ensure that your app calls the correct SDK handler that supports multiple notification handlers. Passing a third party’s notification to
setNotificationRequestorsetNotificationUserInfois essentially a no-op call. The SDK only emits logs indicating the origin of the notification wasn’t from Engagement. -
Geolocation: If you implement multiple SDKs that use location-enabled services, use only one SDK’s location enablement. Using more than one leads to unknown and unsupportable consequences. For example, the methods used by the other providers to interact with iOS
CoreLocationservices and enable location services are likely to affect each provider. An app can monitor a limited number of geofences at any given time. This number depends on iOS version, device type, and other considerations. With multiple implementations competing for a limited resource, the user experience can suffer. Additionally, permissions needed to use location-enabled SDKs can overlap or conflict. -
Feedback: Not all providers are able to detect if a device has been unregistered. To see how notifications are handled using Firebase as a push provider, see the iOS LearningApp.
iOS Data Protection affects the SDK as described in this table.
| iOS Data Protection Level | SDK Behavior |
|---|---|
| No protection | SDK works in the foreground and background |
| Complete until first user authentication | SDK works in the foreground and background after the first unlock |
| Complete unless open | SDK works in the foreground and background after the first unlock |
| Complete | SDK works only in the foreground after the device is unlocked |
The MobilePush SDK requires access to files on the iOS Device file system. Some iOS Data Protection modes can prevent the SDK from accessing the needed files at certain times. During normal operation, the SDK must have access to files while running in the foreground and while running in the background. If the SDK can’t access these files due to an iOS Data Protection mode, an error is logged and file access fails.
By default, the SDK sets the file protection type to NSFileProtectionCompleteUntilFirstUserAuthentication. With this file protection type, files are stored in an encrypted format on disk and can’t be read from or written to until the user unlocks the device for the first time. As of version 8.0.9, the SDK continues to retain the default protection type (NSFileProtectionCompleteUntilFirstUserAuthentication). However, it also provides the capability to override the file protection type within the consuming application. You can choose different file protection types, such as NSFileProtectionComplete and NSFileProtectionCompleteUnlessOpen, based on your specific needs.
NSSQLiteErrorDomain errors can appear in logs if the FileProtectionType is NSFileProtectionComplete and the application goes to the background.
The following example shows how you can override the file protection type.
For an additional example of overriding the file protection type, see the learning application.
If you configure iOS data protection such that the file system isn’t accessible during the SDK configuration call, the SDK retries the call for up to 5 seconds. This retry period allows time for a user to unlock the device and make the file system accessible. If the user doesn’t unlock the device within 5 seconds, an error object is returned describing the error, and the configuration call fails, returning false. In this case, the SDK isn’t configured, and no access to SDK methods must be attempted until the configure method returns true. The error object returns the error code configureDatabaseAccessError.
Certain features of the SDK require access to the file system as the app transitions to the foreground or background. Foreground operations include retrieving messages from Engagement for inbox messaging, location messaging, and sending analytic information back to Engagement. Background operations include sending analytic information back to Engagement. If any of these features are enabled via configuration, then an appropriate iOS Data Protection mode must be selected for them to work correctly.
For iOS applications upgraded from SDK versions 7.x to versions up to 8.0.6, the previous v7.x tags and attributes are retained on the device but not sent to the server. If an application doesn’t reset or regenerate tags and attributes, the device sends empty tags and attributes to the system.
The following sections walk through the requirements for merging datasets successfully.
Using SPM, upgrade to the latest version of the MobilePush SDK for iOS and SFMCSDK for iOS.
The merging tool offers two options to merge attributes and tags: automatic merging and manual merging. In some scenarios, you can choose to defer or avoid merging the datasets. The merging tool defaults to an "opted out" state if you don’t implement either of the merging methods. In the opted out state, tags and attributes aren’t merged from the version 7.x dataset to your current application’s dataset.
The automatic merging option attempts to merge old data into the current dataset, with the current data taking precedence over data within the version 7.x dataset.
The following tables illustrate how automatic merging behaves and how data is merged.
in this tables, key:value pairs are denoted using : as the separator.
Attributes
| Prior Dataset | Current Dataset | Merge Result |
|---|---|---|
| A:B | empty | A:B |
| empty | A:B | A:B |
| A:B, C:D | A:E | A:E, C:D |
| A:B | A: cleared | A: cleared |
Tags
| Prior Dataset | Current Dataset | Merge Result |
|---|---|---|
| SHIRTS | empty | SHIRTS |
| empty | PANTS | PANTS |
| SHIRTS | PANTS | SHIRTS, PANTS |
| SHIRTS | SHIRTS, PANTS | SHIRTS, PANTS |
The following code snippets show you how to configure the SDK to attempt an automatic merge.
To ensure the completion callback passed into setAutoMergePolicy is set before SDK initialization, place the following code snippets before SDK initialization.
The manual merge option enables you to receive both the prior data and the current data in a callback, providing the opportunity to choose what data ultimately ends up in the final dataset.
You can decide what attributes and tags are set in the current dataset. However, to set attributes and tags accordingly, you must retain the data until the SDK is initialized.
Access to the tags and attributes for versions 7.x and 8.x is provided before SDK initialization.
Swift
Objective C
If you must run the merge tool again, you can attempt the merge multiple times.
Reattempting merges doesn’t roll back the current dataset but enables you to regain access to the data within the old version 7.x dataset.
This troubleshooting guidance applies only to MobilePush SDK for iOS versions 8.0.13 and earlier.
Fatal Keychain Access exceptions occur if an application with an active MobilePush SDK integration tries to access Keychain on a locked device secured with Face ID or passcode-based authentication. iOS Data Protection modes prevent the SDK from accessing these files.
These sections describe common Keychain Access exceptions and provide guidance on resolving them.
These are common occurrences of the errSecInteractionNotAllowed exception:
Fatal Exception: com.salesforce.security.keychainException dictionaryItemFromKeychain: Error attempting to look up keychain item: errSecInteractionNotAllowedFatal Exception: com.salesforce.security.keychainException setObject:forKey:: Error saving value to the keychain: errSecInteractionNotAllowed.Fatal Exception: com.salesforce.security.keychainException writeToKeychain: Error adding keychain item: errSecInteractionNotAllowed.
To resolve errSecInteractionNotAllowed exceptions, follow these steps.
-
Upgrade to MobilePush SDK for iOS version 8.0.8 or later and Marketing Cloud SDK version 1.0.6 or later.
-
Before initializing the SDK, set the
setKeychainAccessErrorsAreFatalmethod tofalse.Setting this property to
falselogs the exception to the console instead of causing the app to crash.
You can encounter an error message that indicates a keychain access issue along with an unknown status code (-34018).
To resolve this issue, enable Keychain Sharing in the Signing & Capabilities pane in Xcode. When you enable Keychain Sharing, you don’t need to add identifiers specific to the SDK.
For an example of an ideal SDK implementation on iOS, see the iOS LearningApp.
Not all the code used in the LearningApp is required. Depending on your app, you can decide which parts to use or replicate and which ones to ignore.
These troubleshooting steps apply only to the MobilePush SDK for iOS version 8.0.13 and earlier. In version 8.1.0 and later, the SDK automatically includes the bundle.
When you upgrade to the latest version of the SDK, update MarketingCloudSDK.bundle. If you don’t copy the right versions, your app can crash because the older versions of MarketingCloudSDK.bundle don’t have the required resources.
If you don’t include the latest MarketingCloudSDK.bundle in your app, you can encounter these exceptions.
- NSInvalidArgumentException
Reason:
+entityForName: nil is not a legal NSManagedObjectContext parameter searching for entity name 'SFMCEndpointConfigurationEntity'- NSInternalInconsistencyException
Reasons:
'NSFetchRequest could not locate an NSEntityDescription for entity name 'SFMCEventConfigurationEntity'''Cannot create an NSPersistentStoreCoordinator with a nil model'
To resolve these exceptions, upgrade to the latest version of the SDK and then follow these steps.
- Remove the existing
MarketingCloudSDK.bundlefrom Xcode under Build phases > Copy Resources Bundle. - Based on your integration method, add the latest
MarketingCloudSDK.bundle.- If you’re using SPM as a dependency manager, following the instructions provided in the iOS Migration Guide.
- If you’re using other integration methods, follow the guidance in the Quickstart Guide for iOS.
Silent push notifications are delivered without an alert message or sound, typically to trigger updates to the app UI or background operations. A silent push notification wakes your app from a "Suspended" or "Not Running" state to update content or run certain background tasks without notifying users.
To use silent push notifications to trigger background tasks, configure your app to receive notifications even when it’s in the background. To do so, navigate to the Signing & Capabilities pane on Xcode, and add the Background Modes capability to the main app target. Also ensure that you select the Remote notifications checkbox.
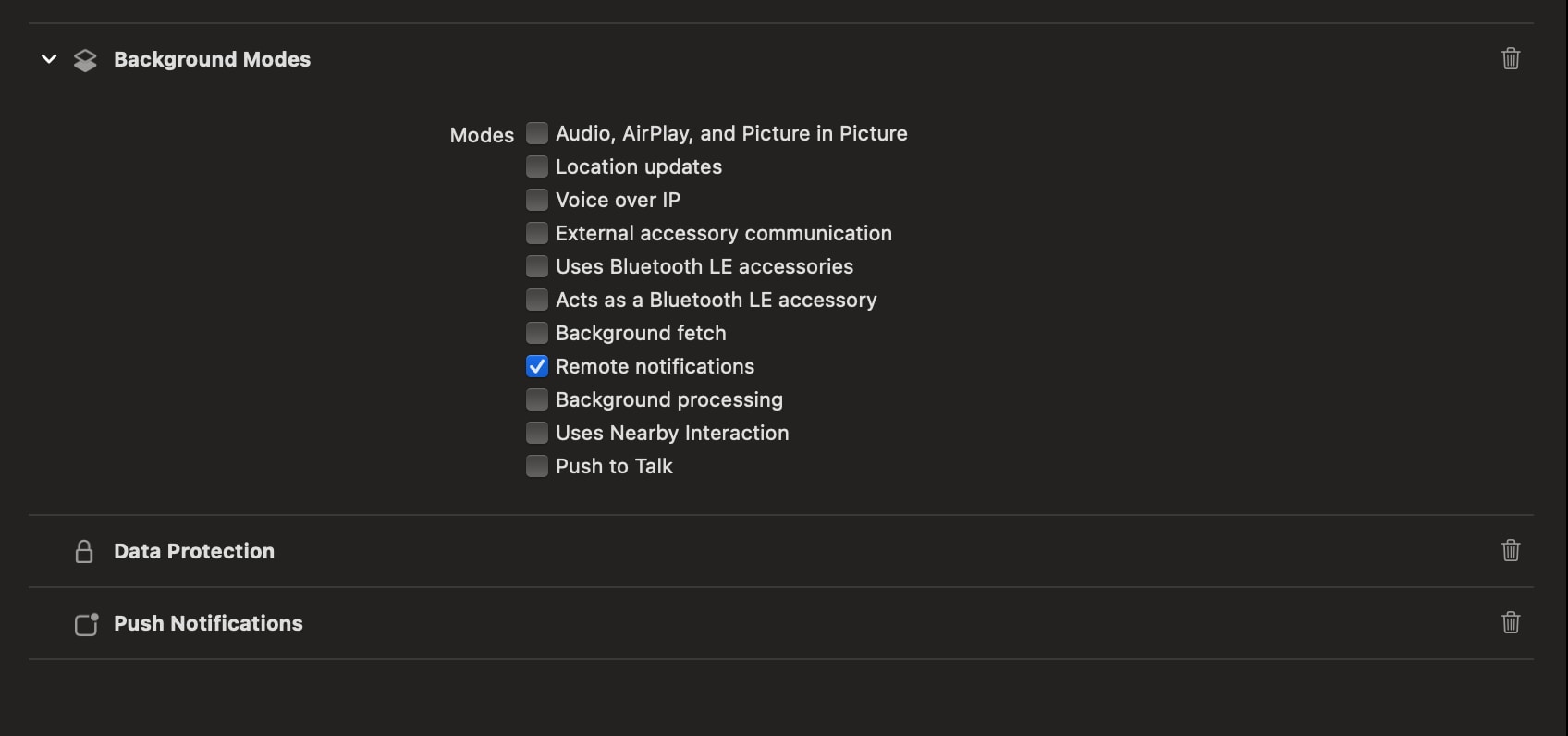
To handle silent push notifications, implement the application:didReceiveRemoteNotification:fetchCompletionHandler: application delegate method. For more information, see Apple’s documentation on Pushing background updates to your app.
If you encounter issues with push delivery analytics, consider these common problems and their resolutions:
- Missing Push Delivery Analytics
- First confirm that push delivery analytics is enabled in the Engagement UI. If disabled, your Engagement admin must enable it for the SDK to send delivery events.
- If push delivery events and analytics aren’t appearing in your Engagement reports, verify whether you’re sending supported message types. Push delivery analytics are only available for Push and Alert + Inbox messages. In-App, Geofence, Proximity, and silent pushes aren’t tracked.
- Multiple Push Provider Implementation Problems
If you’re using multiple push providers, ensure that no fields or keys are removed from the push payload before passing it to
SFMCNotificationService, which yourNotificationServiceclass in the service extension inherits from. The SDK requires the complete push payload to process push delivery events. If any keys or fields are missing, the SDK logs a warning and doesn’t process the push delivery event.