Set Up Amazon RDS to Access Data from Salesforce
Before you set up Amazon RDS to integrate with Salesforce, understand the considerations for GraphQL services to be compatible with Salesforce. The Lightning Experience provides a set of tools to manage structured data. Admins can create flows, reports, list views, and more with just a few clicks. The robust user interface is powered by a sophisticated data store, which is highly flexible to query data. If the data source is external to Salesforce and exposed via GraphQL, the GraphQL service must support the same set of operations to power the user interface.
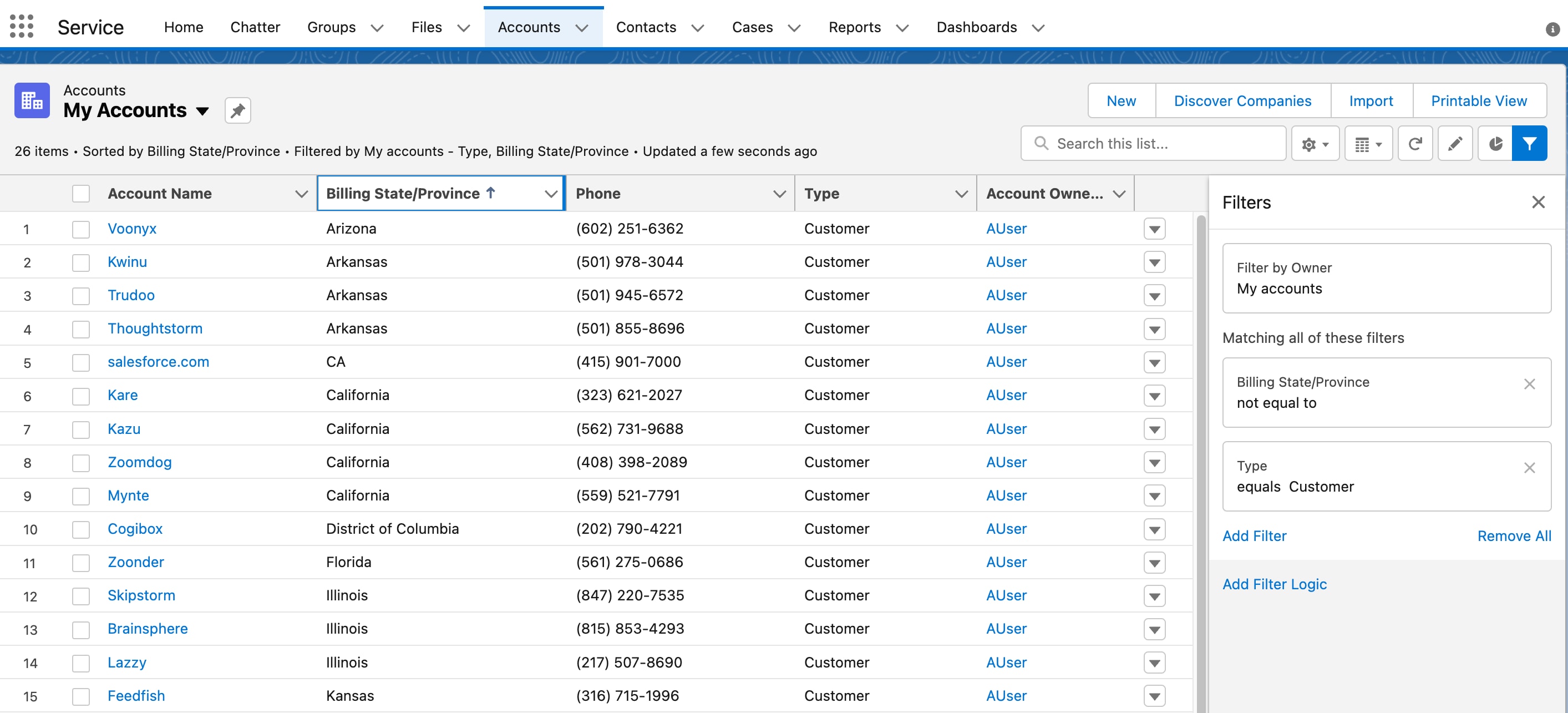
This example image shows a list view that filters the list of Accounts by several fields, and then sorts by Billing State/Province. If a large number of results match the filter criteria, the list is paginated. To enable this user experience, the underlying external data store must support the operations.
The compatibility considerations for GraphQL services are similar to the Custom Adapter for Salesforce Connect, which enables developers to write Apex code and handle requirements such as unique IDs, pagination, sorting, filtering, and aggregation. To help developers deliver the equivalent functionality via GraphQL, Salesforce and Amazon collaborated to create a template. Use the template to easily deploy to an AWS account and extend to your own database tables.
Complete these setup tasks for Amazon RDS to connect with the Salesforce Connect adapter for GraphQL and access external data in Salesforce.
-
Obtain an AWS account that you can use to set up and test your configuration. If you don’t have an AWS account, see How do I create and activate a new AWS account?
-
Run our AWS CloudFormation template to set up the Amazon AppSync GraphQL schema for integration with Amazon RDS. This AWS Partner Network Blog Post walks you through the steps.
- Use this CloudFormation template to deploy this to a new Virtual Private Cloud (VPC) in your AWS account.
- Use this CloudFormation template to deploy this to an existing Virtual Private Cloud (VPC) in your AWS account. Note that you’ll need to supply the identifier for the VPC during the install process.
-
Note the Amazon Resource Name (ARN) from the Secrets Manager. A secret stores the credentials to access the database instance via AppSync GraphQL API. The secret captures the administrative password of the Amazon RDS database. You can find the ARN for your secret in the Secrets Manager console on the secret details page.
-
Open the Secrets Manager console.
-
From the list of secrets, choose your secret.
Based on the configuration, the secret would be /graphqlrdsserverless/dbsecret (for ServerlessCluster) or /graphqlrds/dbsecret (for StandardCluster).
-
Under Secret ARN, locate and copy the ARN.
-
-
Validate the Amazon RDS configuration with a test SQL query.
- From the AWS Console, go to your Amazon RDS.
- On the navigation menu, choose the Query editor.
- Under Database instance or cluster, find and connect to your database cluster.
- Under Database username, choose Connect with a Secrets Manager ARN.
- Enter the ARN that you noted from the Secrets Manager.
- Enter the name of the database as graphqlrds or graphqlrdsserverless.
- Enter this SQL query in the query window, and choose Run to validate the RDS configuration.
-
Test the AppSync API’s connection to the database with a GraphQL query.
- Open the Amazon AppSync console, and choose the GraphQL API that AWS CloudFormation template created.
- Choose the Queries tab.
- In the Queries pane, paste this GraphQL query.
This example GraphQL query is functionally the same as the SQL query executed to validate the Amazon RDS configuration.
-
Choose Execute query (the orange play button). It can take a few minutes for the first set of the query results to appear in the results pane because of Lambda’s cold start.
-
Test the authentication setting of the AppSync’s GraphQL API when an HTTP call originates from outside the AWS console. To validate connectivity and authentication for an HTTP call that the Salesforce Connect adapter makes to Amazon AppSync, ping the GraphQL API endpoint with the API key using this curl (or Postman). Note the API key to store as the authentication parameter for an external credential principal in Salesforce.
If the authentication settings are validated, the data returned must look similar to this result (formatted for readability).