Private SLAS Client Use Cases
Setting up SLAS and making your first request is covered in the Get Started guides. See Authorization for Shopper APIs.
The following use cases show how SLAS enables authorized access to a Shopper API for private clients under different login scenarios.
Remember that any shopping app that is able to securely store a client secret is a private client. Full stack web apps and all shopping apps with a backend-for-frontend (BFF) must be provisioned as private clients.
Each use case demonstrates a different login scenario: guest user (no login), federated login, and B2C login.
Although all three use cases feature OCAPI’s /baskets endpoint, remember that a SLAS access token can be used with any Shopper API endpoint.
Each step in the authentication flow is numbered and described in detail for all three use cases. The numbered steps are also illustrated with a diagram to help you visualize the process.
See the API specification for full details on how to make your API requests.
You can explore these use cases interactively with a Postman collection: Salesforce Commerce B2C SLAS Use Cases.
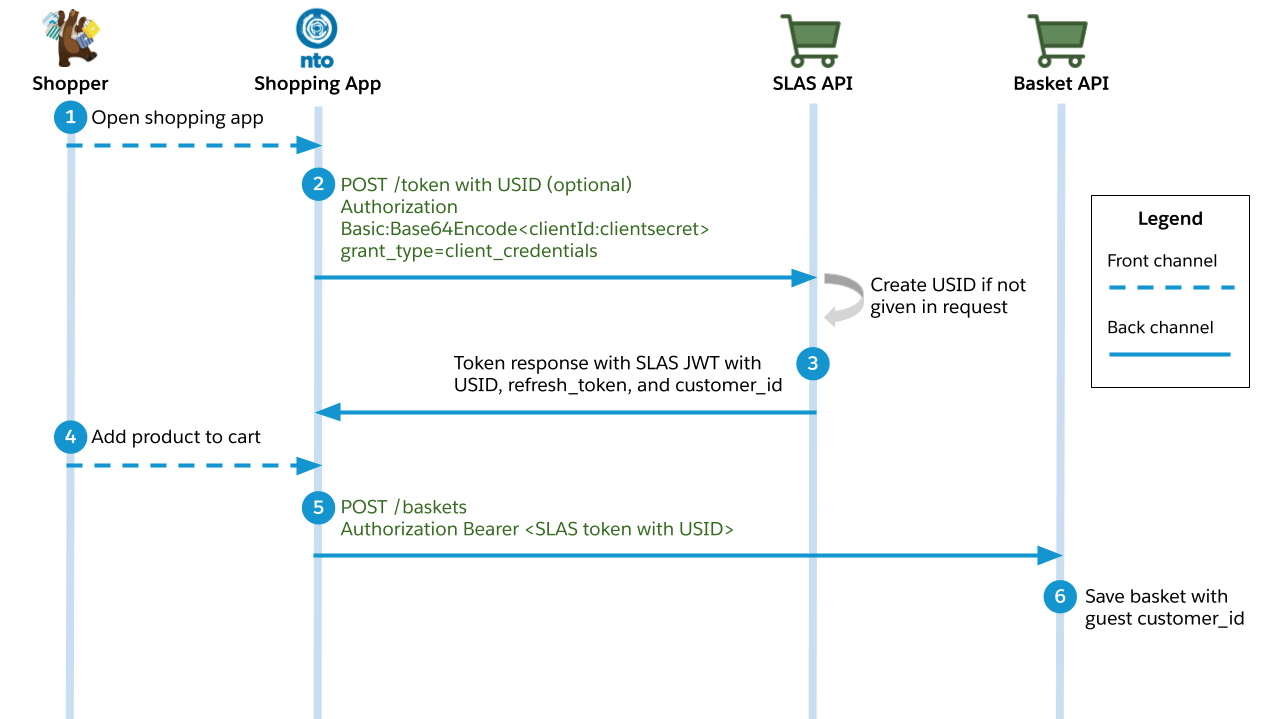
This use case describes what happens when the shopper adds a product to their basket without logging in first. It follows the client credentials grant flow as defined by the OAuth 2.1 standard.
-
A shopper opens a Commerce Cloud shopping app and starts interacting with it.
-
The shopping app requests an access token using the
/tokenendpoint of the SLAS API.- The request must include an authorization header that contains a Base64 encoded version of the following string:
<clientID>:<clientSecret>. (Don’t forget to replace<clientID>and<clientSecret>with actual values before encoding the string.) - Example header value:
Authorization: Basic czZCaGRSa3F0MzpnWDFmQmF0M2JW. - The client ID and client secret must be provisioned for the app by a SLAS Organization Administrator. See the SLAS Admin API for more information.
- Required query parameter:
grant_type=client_credentials. - Recommended query parameter (will be required in the future):
channel_id. - Optional query parameter:
usid. If you already have a Unique Shopper Identifier (USID) for the guest user, you can pass it in. Otherwise, a USID is for you by SLAS. - Best practice: reuse the USID for a shopper from the previous guest login so that you can tie that user to all the previous login attempts and enable personalization.
- The request must include an authorization header that contains a Base64 encoded version of the following string:
-
The endpoint responds with an access token in the form of a JSON Web Token (JWT), a
customer_idstring, a USID, and a refresh token. -
The guest shopper adds a product to their basket.
-
The shopping app makes a request to the
/basketsendpoint of OCAPI and provides a SLAS access token in the header. -
The Baskets API saves a shopping basket with a
customer_idstring that is associated with the guest user.
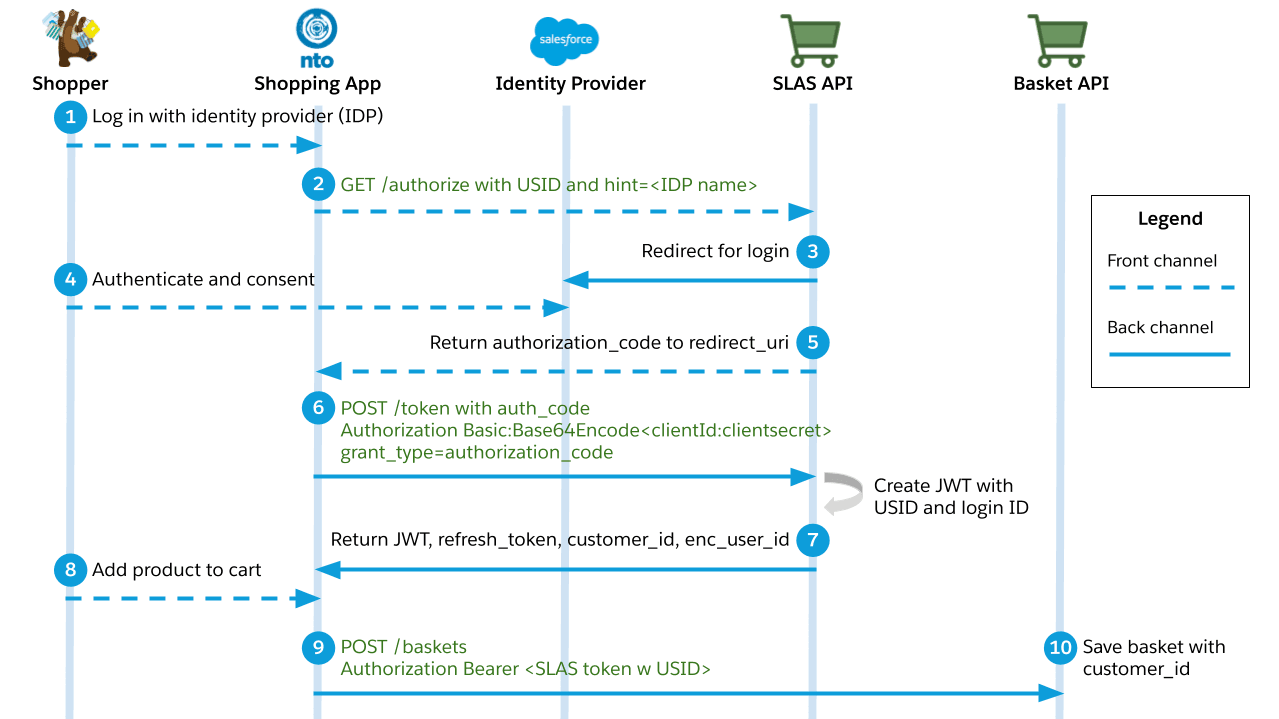
This use case describes what happens when a shopper logs in using a third-party identity provider before adding a product to their basket. It follows the authorization code grant flow as defined by the OAuth 2.1 standard.
-
A shopper logs in to a Commerce Cloud shopping app and chooses a third-party identity provider (IDP) to perform the authentication.
-
The shopping app makes a request to the
/authorizeendpoint of the SLAS API.- Required query parameters:
hint,response_type=code,client_id, andredirect_uri. - The
hintparameter specifies the name of the identity provider. - The
redirect_uriparameter specifies what app route to redirect to when the login is complete.
- Required query parameters:
-
The SLAS API redirects to the identity provider’s login page.
-
The shopper enters their credentials and consents.
-
If login is successful, the SLAS API responds with an authorization code and redirects to the shopping app.
-
The shopping app requests an access token using the
/tokenendpoint of the SLAS API.- The request must include an authorization header that contains a Base64 encoded version of the following string:
<clientID>:<clientSecret>. (Don’t forget to replace<clientID>and<clientSecret>with actual values before encoding the string.) - Example header value:
Authorization: Basic czZCaGRSa3F0MzpnWDFmQmF0M2JW. - The client ID and client secret must be provisioned for the app by a SLAS Organization Administrator. See the SLAS Admin API for more information.
- Required query parameter:
grant_type=authorization_code.
- The request must include an authorization header that contains a Base64 encoded version of the following string:
-
The endpoint responds with an access token in the form of a JSON Web Token (JWT), a
customer_idstring, a USID, and a refresh token. -
The shopper adds a product to their basket.
-
The shopping app makes a request to the
/basketsendpoint of OCAPI and provides a SLAS access token in the header. -
The Baskets API saves a shopping basket with a
customer_idstring that is associated with the registered user.
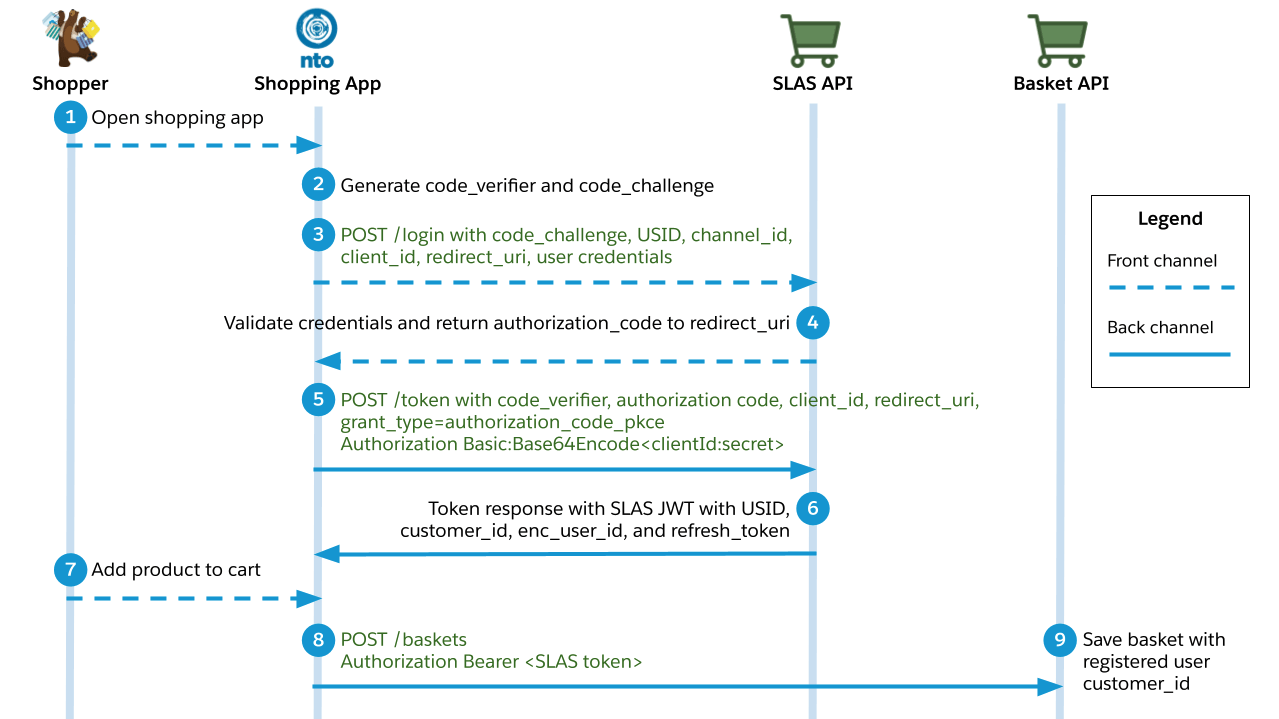
This use case describes what happens when a shopper logs in with credentials that are managed by a B2C Commerce instance before adding a product to their basket. It follows the authorization code grant flow as defined by the OAuth 2.1 standard. It also uses a proof key for code exchange (PKCE), as defined by RFC 7636.
-
A shopper logs in to a Commerce Cloud shopping app and chooses to authenticate directly through the shopping app.
-
The shopping app generates two strings:
code_verifierandcode_challenge.- The
code_verifierstring is a random string. - The
code_challengeis an encoded version of thecode_verifierstring using an SHA-256 hash.
- The
-
The shopping app makes a request to the
/loginendpoint of the SLAS API.- The request must include an authorization header that contains a Base64 encoded version of the following string:
<shopperUserID>:<shopperPassword>. (Don’t forget to replace<shopperUserID>and<shopperPassword>with actual values before encoding the string.) - Example header value:
Authorization: Basic czZCaGRSa3F0MzpnWDFmQmF0M2JW - Required query parameters:
code_challenge,usid,channel_id,client_id, andredirect_uri.
- The request must include an authorization header that contains a Base64 encoded version of the following string:
-
The SLAS API validates the user credentials, redirects to the redirect URI, and returns an authorization code.
-
The shopping app makes a request to the
/tokenendpoint of the SLAS API.- The request must include an authorization header that contains a Base64 encoded version of the following string:
<clientID>:<clientSecret>. (Don’t forget to replace<clientID>and<clientSecret>with actual values before encoding the string.) - Example header value:
Authorization: Basic czZCaGRSa3F0MzpnWDFmQmF0M2JW. - The client ID and client secret must be provisioned for the app by a SLAS Organization Administrator. See the SLAS Admin API for more information.
- Required query parameters:
grant_type=authorization_code_pkce,code_verifier,code,client_id, andredirect_uri.
- The request must include an authorization header that contains a Base64 encoded version of the following string:
-
The endpoint responds with an access token in the form of a JSON Web Token (JWT), a
customer_idstring, a USID, and a refresh token.- The response also includes an
enc_user_idstring that can be used to call Einstein APIs.
- The response also includes an
-
The shopper adds a product to their basket.
-
The shopping app makes a request to the
/basketsendpoint of OCAPI and provides a SLAS access token in the header. -
The Baskets API saves a shopping basket with a
customer_idstring that is associated with the registered user.
Now that you’re familiar with the use cases with private clients, check out the Public SLAS Client Use Cases.
When you’re ready to incorporate SLAS into your app, explore the API reference for the complete technical specifications for the SLAS endpoints.