Session Bridging Overview
Clients can interact with the B2C Commerce platform using controllers, HTTP APIs, or both. Controllers and APIs use different authentication and authorization (authnz) methods, which means you must “bridge” the different authnz methods in hybrid implementations to keep them in sync for shopper login, logout, and other shopper-related events.
This topic provides an approach for “session bridging” using a hybrid SCAPI/OCAPI and B2C Commerce controller implementation. You can use this approach as a guide when working with PWA Kit or any other headless Backend for Frontend (BFF). For additional session bridging instructions that apply when using a hybrid implementation (SiteGenesis/SFRA and PWA Kit), see Phased Headless Rollouts. In our case, session bridging involves synchronizing a SLAS JWT (for SCAPI) with a session dwsid (for B2C Commerce controllers), or vice versa. At any time, the browser must be able to make a request to either the controller or an API and be recognized as the same shopper.
Note: SLAS tokens can be used with all SCAPI and OCAPI Shopper APIs, but using SCAPI is preferred.
Only existing customers can access some of the links on this page. Visit Salesforce Commerce Cloud GitHub Repositories and Access for information about how to get access to the Commerce Cloud repositories.
This section outlines the authnz methods for a headless implementation using PWA Kit and hybrid authentication (Hybrid Auth), providing a guide for other headless implementations.
As of B2C Commerce 25.3, Hybrid Auth is the functional equivalent and replacement for Plugin SLAS.
PWA Kit uses SCAPI for authnz, while B2C Commerce controllers use Hybrid Auth. For details, see Hybrid Authentication and Phased Headless Rollouts.
Make sure you:
- Understand the authnz methods of whatever components you include in your headless implementation.
- Minimize the use of session bridging (POST sessions and POST customers/auth). Only create a session if necessary and reuse existing sessions for as long as possible.
- For optimal performance, apply the same approach to JWT creation for SCAPI/OCAPI calls.
Summary of SCAPI and B2C Commerce controller authnz mechanisms:
| Client Access | Access Method | Expiry Time | Refresh Token |
|---|---|---|---|
| SCAPI | Retrieve SLAS access tokens (in the form of a JWT): | JWT access tokens are valid for 30 minutes. | For up to 90 days, you can use the refresh token provided by SLAS to get a new access token. |
| Controllers | Use sessions that are identified by HTTP cookies prefixed with dw. The dwsid cookie contains your Session ID and is used by the server to locate your session. |
| N/A |
Basket lifetime is different from session lifetime and configured separately. To learn more see Configure Basket Preferences.
You must perform session bridging for various lifecycle events, for example: when a shopper first lands on a storefront, when a shopper subsequently logs in or out, and when tokens or sessions expire.
The call flows that are detailed in the following sections are the flows that PWA Kit and Hybrid Auth (the functional equivalent and replacement for Plugin SLAS) use. The purpose of these flows is to obtain a JWT (SLAS access token) and a dwsid (session) that reference the same shopper, so that subsequent requests are in sync, regardless of whether those requests come from an API or a controller.
These flows are for new shoppers who have never before visited your storefront. The series of calls you must make depends on whether a shopper first lands on a headless/PWA site or the B2C Commerce (SFRA) site.
You can choose to store the refresh token in different ways, including persisting the SLAS JWT and refresh token on your BFF or, alternatively, sending them back to the client. For all flows discussed in our approach, it is assumed that the SLAS refresh token that is associated with the shopper is stored in a cookie that is accessible both from the server and from JavaScript.
In our case, we are using PWA Kit, but the following guidance applies to any BFF:
- Get a JWT From SLAS. Depending on whether you’re using a public or private client, the flow varies. If you use a SLAS private client, you only need to call
getAccessToken.- Call SLAS
authorizeCustomer(oauth2/authorize) - Call SLAS
getAccessToken(oauth2/token)
- Call SLAS
- You now have a SLAS token, which includes a JWT that you can use to access the APIs, and a refresh token you can use to get a new JWT.
- Call OCAPI Shop
/sessions. - You now have a cookie with a
dwsidthat is associated with your JWT.
With a SLAS access token and a Session ID, you can make requests using either APIs or controllers.
The following image shows the request flow for new shoppers landing on a headless site:
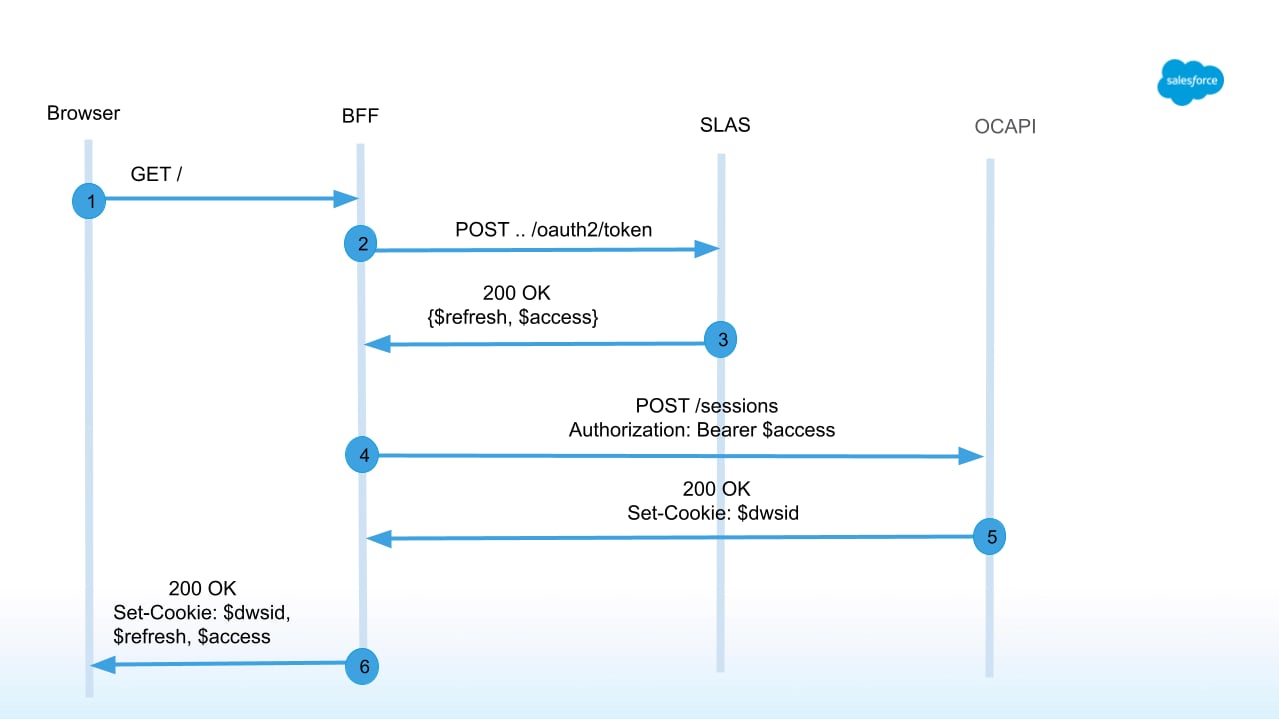
In this flow, the browser makes a request to B2C Commerce, which automatically creates a session and returns a dwsid for any request that meets the following criteria:
- Doesn’t contain a DWSID cookie.
- The session referenced by the cookie is expired or otherwise invalid.
Use Hybrid Auth, which is the functional equivalent and replacement for Plugin SLAS, or manually perform the following steps:
- Get a JWT From SLAS. Depending on whether you’re using a public or private client, the flow varies. If you use a SLAS private client, you only need the token call, not the authorize call.
- Call SLAS
authorizeCustomer(oauth2/authorize) - Call SLAS
getSessionBridgeAccessToken(oauth2/session-bridge/token)
- Call SLAS
- You now have a SLAS token, which includes a JWT that you can use to access the APIs, and a refresh token you can use to get a new JWT.
The following image shows the request flow for new shoppers landing on a B2C Commerce site:
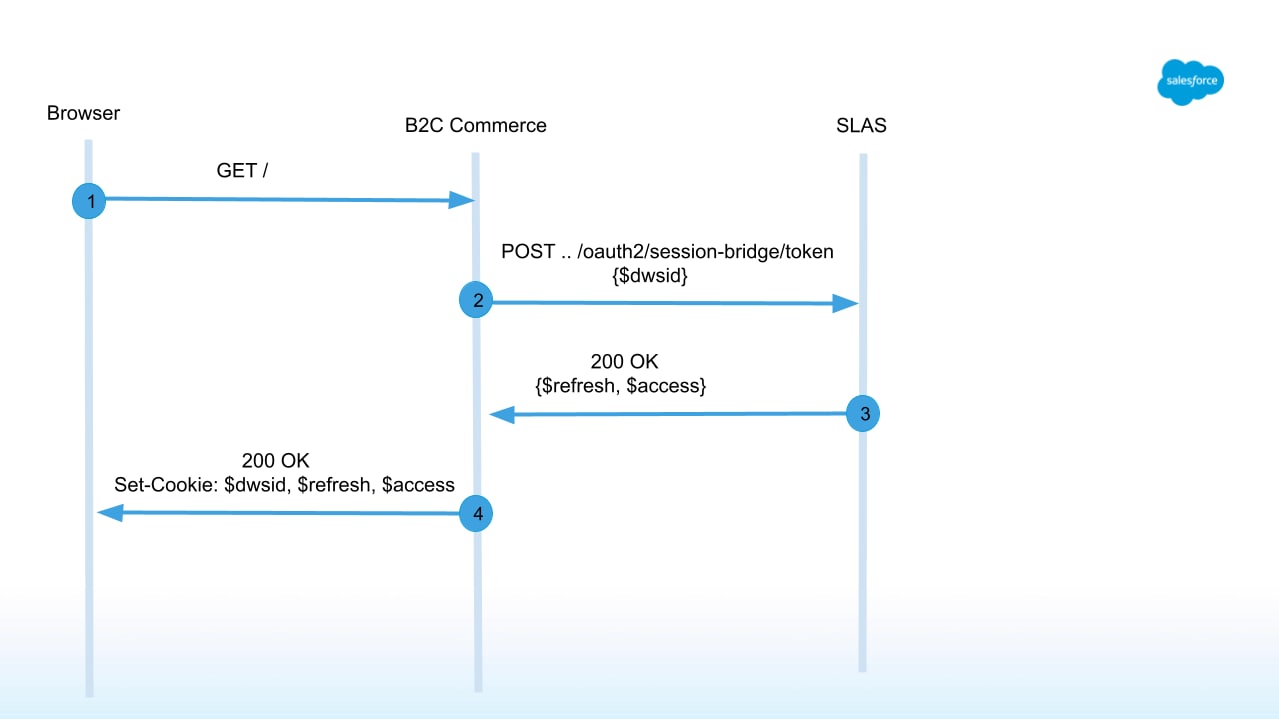
Returning guest and returning registered shopper flows are the same, but the sequence of calls depends on whether the shopper first landed on the headless storefront or B2C Commerce.
- Use the SLAS refresh token to call SLAS
getAccessToken(oauth2/token?refresh_token=...) - Call OCAPI Shop
/sessionsto get new DW cookies for the shopper.- Now you've got both an access token and a session to call APIs or controllers. The returning shopper is now logged in again.
The following image shows the request flow for the returning shopper on the headless site:
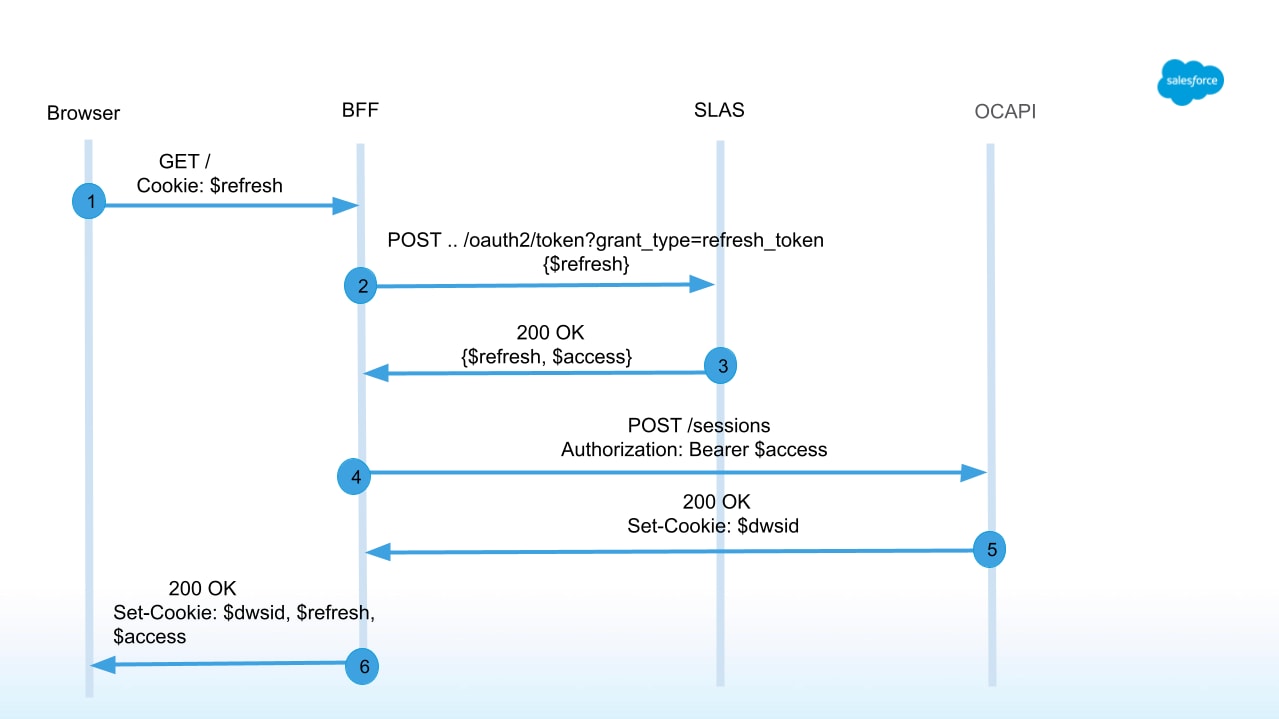
If your browser doesn’t have a dwsid in its cookie jar to send, or the dwsid that you send is invalid or expired (maximum session life is six hours), then you will get a new session when the request is made to B2C Commerce and you must perform session bridging.* *
Use Hybrid Auth, which is the functional equivalent and replacement for Plugin SLAS, or manually perform the following steps:
- Use the refresh token to call SLAS
getAccessToken(oauth2/token?refresh_token=...) - Call OCAPI Shop
/sessionsto get new DW cookies for the shopper. - Reload the page. This forces the page to be rendered using the newly acquired session.
The following image shows the request flow for a returning shopper on B2C Commerce:
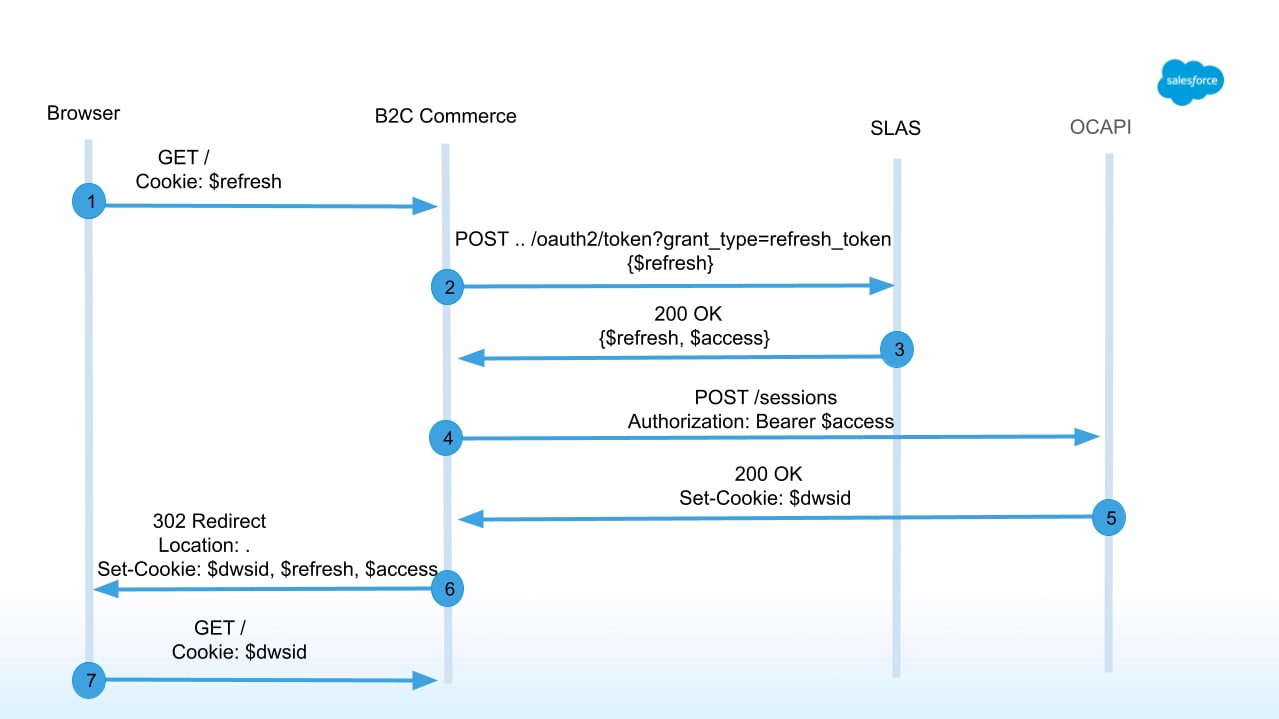
If a guest shopper logs in, the sequence of calls you need to make depends on whether the shopper logs in to the headless storefront or B2C Commerce.
If the guest shopper logs in to the headless storefront:
- Provide the user's credentials to login with oauth2/authorize. At that point, you'll have a JWT for the logged in shopper.
- Whatever
dwsidyou currently have references the guest session, which means it is stale.- Call OCAPI Shop
/sessionswith the logged in JWT to retrieve adwsidfor the logged-in shopper.
- Call OCAPI Shop
If the guest shopper logs in to B2C Commerce (SFRA):
- Provide the user's credentials to login with oauth2/authorize. At that point, you'll have a JWT for the logged in shopper.
- Call OCAPI Shop
/sessionswith the logged in JWT to retrieve adwsidfor the logged-in shopper. - Return a redirect to the shopper so the page is re-rendered with the updated session.
When a shopper logs out of your storefront, the sequence of calls you need to make depends on whether the shopper logs out of the headless storefront or B2C Commerce.
If the shopper logs out of the headless storefront:
- Discard the current JWT and refresh token. You can log the customer out using the loguoutCustomer endpoint.
- Obtain a new guest JWT using
getAccessToken. - Call OCAPI Shop
/sessions.
If the shopper logs out of B2C Commerce (SFRA):
- The existing session is automatically cleared.
- However, the JWT still is logged in. Obtain a new guest JWT using
getAccessToken.
SLAS access tokens are good for 30 minutes from the time they are granted. You can decode the JWT and look at the exp field for the exact timestamp.
After 30 minutes elapses, the token can no longer be used to make an API request. If you make a request with an expired JWT, an error is thrown.
- Use the refresh token to call SLAS
getAccessToken(oauth2/token?grant_type=refresh_token) to get a new token.- Note: Refresh tokens from public clients can only be redeemed once, while refresh tokens from private clients can be used for multiple days.
- For
prdinstances, refresh tokens are good for 90 days. For other instances, refresh tokens are good for nine days. The exact value can be found in TokenResponse's refresh_token_expires_in property.
- When the session expires due to a timeout, the next call to B2C Commerce results in the OnSession hook firing, so this will be the same as the returning visitor scenario.
- Returning Shopper on B2C Commerce (SFRA)